The Inconvenience of 2FA Convenience
18 Jul 2023A common piece advice in the security world for securing your accounts/services is to use 2-Factor Authentication (2FA). “Use 2FA to be safe!” slogan often fails to take into account that many/most people have the second factor authentication on the same device that houses the first factor authentication.
Some quotes from the Web about 2FA:
2FA is essential to web security because it immediately neutralizes the risks associated with compromised passwords. [1]
Using multi-factor authentication blocks 99.9% of account hacks [2]
The use of multi-factor authentication (MFA) could prevent as much as 80–90% of cyber-attacks[3]
These types of advice and quotes are plenty in magazines, forums and all around the web. Someone reading this might easily assume that using 2FA automatically guarantees safety and security.
Let’s imagine a scenario: While heading to Borough Market in London on a Saturday afternoon, you decide to take out your phone to check WhatsApp and send a message. The next thing you know, your phone is stolen. Unlikely? Well, according to official figures, a phone is reported stolen in London every six minutes. [4][5] Thieves in London often snatch phones on their bicycles or mopeds, preying on victims who are walking on the street with phones in their hands.
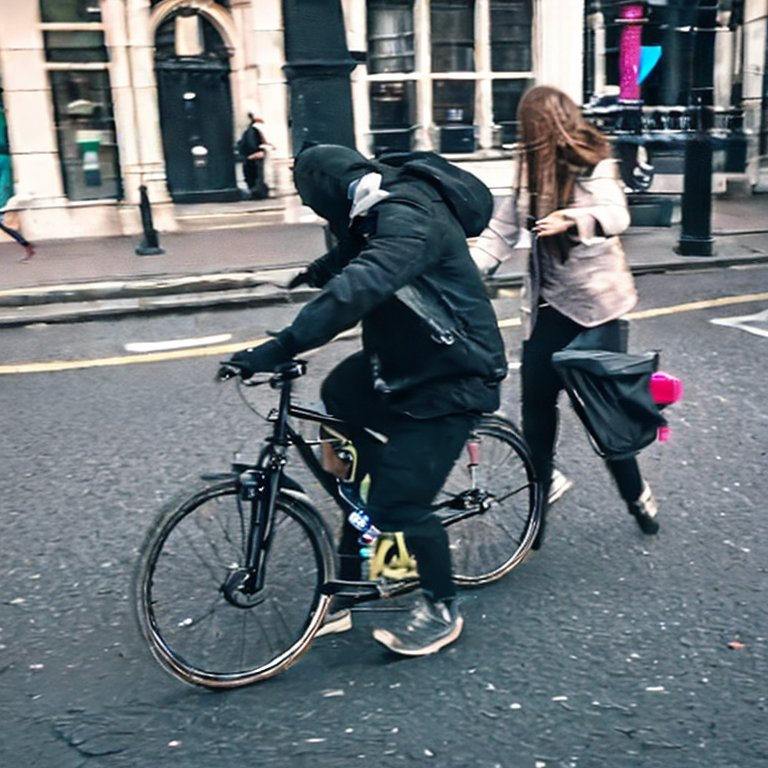 Image generated by Stable Diffusion - Thief on bike snatching phone from walking person in London, photography, two people, 4k, 8k
Image generated by Stable Diffusion - Thief on bike snatching phone from walking person in London, photography, two people, 4k, 8k
Thieves used to primarily target phones to resell them for parts, but times have changed. More and more people become victims of “crypto muggings”[6], money stolen from bank accounts, data theft. Just think about the amount of important data an average person has stored in Gmail, Dropbox and phone itself? If a malicious person were to gain access to your inbox and 2FA app on your phone, could they potentially access your accounts and steal your money?
Consider this: a thief who stole your unlocked phone (we will discuss this in details later) likely has access to Google Auth app, your SIM number and your passwords, that are synced in the browser. This is more than enough to take over your online accounts, drain your crypto etc
Threat modeling - IRL style
I will start this section by sharing what prompted me to write this article. Recently, I traveled to Washington, DC, and on the second day of travel, I dropped my phone. Fortunately, I was already checked into the hotel. Unfortunately, I cracked my phone screen. This is where the tale of the Threat Modeling article begins. For anyone who is not familiar with or intimidated by the term “Threat Modeling,” I’ve provided links at the bottom of this article explaining what it’s.
Threat modeling is likely something you’ve already done, even if you are not aware of this specific terminology. Simply put, Threat Modeling is a process of understanding what can go wrong and what you can do about it. [This is an oversimplified explanation.]
 Random pic from the trip
Random pic from the trip
Scenarios:
1) I could use a backup phone/buy a new phone and re-login to important services/apps
2) Try to get the phone screen repaired ASAP
3) Be without a phone for the next 3 days
Before we discuss each scenario in detail I would like to talk about Threat modelling of the 2FA setup and how it affects scenarios above.
A Threat Model, by User Persona
Let’s take a look at 2FA security from the attacker’s point of view.
When making a decision on how your 2FA setup should look, it would be useful to understand what you are trying to achieve and how much time and effort you are willing to put in.
Similarly to the Bicycle Threat Model article [7], I would like to threat model by considering each kind of attacker in turn, making assumptions about their level of competence and motivation, i.e., by “attacker persona.” By understanding what type of attackers we are likely to face, we can improve our threat model. This type of Threat Modeling has its limitations, but it will be covered in a separate Threat Modeling blog post.
From a 2FA security point of view, there are four types of attackers you, as the average user, are most likely to face:
“Phish McPerson,” remote attacker trying to phish you
McPerson is an attacker who is trying to gain access to your accounts remotely. McPerson loves to send emails pretending to be from websites you are familiar with. “You have a £10000 charge on your card. Please click here to authorize or cancel” - their favorite SMS.
“Malwareena Jones,” remote attacker who is more technically capable than Phish McPerson
Malwareena Jones knows how to perform more things than Phish McPerson: SIM hijacking, 2FA specific attacks. Jones got her username because in the past she used malware to steal 2FA codes.
“Bandit Bob,” criminal who loves bicycles
Bob loves to snatch phones from people who walk around town, with the phone in their hands, but he also doesn’t mind watching you type the PIN code when you are unlocking your phone and stealing the phone sneakily later. When in a cafe or a bar, how often do you leave your phone on the table? Well, this is one of the favorite places for thieves to steal your phones. [8]
Smashing Sam, criminal who isn’t afraid to use muscles
Smashing Sam used to be somewhat of a fighter back in the day, but now prefers to use her muscles in illegal ways. She can threaten you to unlock your phone and transfer money or give your password.
Coming up with better advice based on Phish McPerson, Malwareena Jones, Bandit Bob, Smashing Sam
In order to have a more secure setup, we need to take steps against all four imaginary attackers.
Phish McPerson can be secured against by:
- Using a custom DNS server to block malicious domains - PiHole [9] and NextDNS[10] can subscribe to blocklists, so new malicious domains get blocked on the DNS level.
- Using an ad blocker plugin for your browser - This is even recommended by the FBI [11].
- Being vigilant when receiving emails, texts, and calls.
- [Optional] Having a separate device for all important services. For example, a separate, hardened laptop that is only used to log in to banking, government, and other applications. This way, you have all important links saved and don’t need to click on anything to avoid getting phished
Malwareena Jones can be secured against by:
- Whenever presented with a choice between a 2FA app or SMS for the 2FA, always choose the 2FA app.
- Contacting your SIM card provider and asking them to lock your SIM. This could mean that if you lose your SIM card, you will have to do additional things to get it back. You might also put a PIN on your account (though many people say this is useless).
- Porting your number to a provider that is less likely to easily give your SIM card away.
- Unless required, don’t provide your phone number to services you use a lot [12].
- Following the advice against Phish McPerson above.
- [Optional] Similarly to Phish McPhishing defense, consider using a separate, hardened device to interact with important services.
Bandit Bob can be secured against by:
- Having a 2FA app on a device stored in a secure location, like home, or having a second, locked phone that you carry with you but don’t use in public. Even if this phone is snatched or stolen from you, the phone is locked, so it’s less likely a thief is able to extract keys and passwords.
- Having a separate user profile on your phone. https://source.android.com/docs/devices/admin/multi-user
- When you need to use your phone in public, check your surroundings.
- Don’t leave your phone on the table in public spaces.
Smashing Sam can partially be secured against by:
- Following everything listed for Bandit Bob.
- Having your 2FA stored in a safe place and not carrying it with you. For example, locked at home/safe.
- Staying vigilant whenever possible.
- Having secondary physical security controls - a higher level, the actions you take are all geared towards making it physically impossible for you to compromise/give away access even if they try to strongarm you into doing so
- Implementing secondary physical security controls - taking actions to make it physically impossible for someone to compromise or obtain access, even if they use intimidation tactics. This is a higher level of security than other measures.
The majority of people are most likely to encounter Phish McPerson and Bandit Bob. Unless it’s a targeted attack, it’s unlikely that you will be targeted by Smashing Sam or Malwareena Jones for the sole purpose of stealing your 2FA.
Creating Your Own Threat Model vs Universal Advice
When faced with a choice on how to secure your 2FA setup or anything else, the logic remains the same: what can be done and how likely am I to follow this advice?
Some level of threat modeling is much better than no threat modeling at all. Think of it like exercising - often it’s better to exercise at least a bit than not to exercise at all. Develop your own 2FA strategy that is both secure and likely to be followed daily.
To wrap up this article, I wanted to share what happened to my broken phone and how it ties to my personal strategy.
After my phone screen got cracked, I was presented with three choices:
- I could use a backup phone or buy a new one and re-login to important services.
- Try to get the phone screen repaired ASAP.
- Be without a phone for the next three days.
Option 3 was not viable for me, as I needed to access my personal email and other things.
Option 2 ended up being impossible, as none of the nearby phone screen repair services could replace the screen quickly enough.
Thankfully, my colleague Pavan helped me (a big thanks to him) and took me to BestBuy, where I bought a temporary phone. However, after getting the new phone, I was presented with an issue: my 2FA device is stored in a secure location, which I don’t have access to, nor do I have access to my password manager. Thankfully, my 2FA setup allowed for this scenario. Without going into too much detail, using a one-time pad [14], my laptop, secure line and an authorized/trusted person, I was able to regain access to my accounts. Having a support network, such as a collegue or trusted individual can be a valuable factor when doing TM.
There are several new developments that are gaining traction that will significantly alter how many of us organize our two-factor authentication (2FA) setups. These include Passkeys, WebAuthn, as well as older measures like hardware keys such as Yubikey. However, as there are already great articles covering those, they will not be covered in this blog post. Instead, they will be included in the further reading section below.
This article is heavily inspired by https://calpaterson.com/bicycle-threat-model.html. Check it out for a fantastic read! References:
[1] https://www.bu.edu/tech/support/information-security/why-use-2fa/
[3] https://www.infosecurity-magazine.com/news/tech-execs-mfa-prevent-90-of/
[4] https://www.bbc.com/news/uk-england-london-65105199
[5] https://www.theguardian.com/money/2012/jan/20/phone-snatchers-iphones-thieves-bikes
[7] https://calpaterson.com/bicycle-threat-model.html
[10] https://nextdns.io
[11] https://www.ic3.gov/Media/Y2022/PSA221221
[12] https://news.ycombinator.com/item?id=29742970
[14] https://en.wikipedia.org/wiki/One-time_pad
Further reading:
https://shostack.org/resources/threat-modeling
https://owasp.org/www-community/Threat_Modeling
https://news.ycombinator.com/item?id=36712497